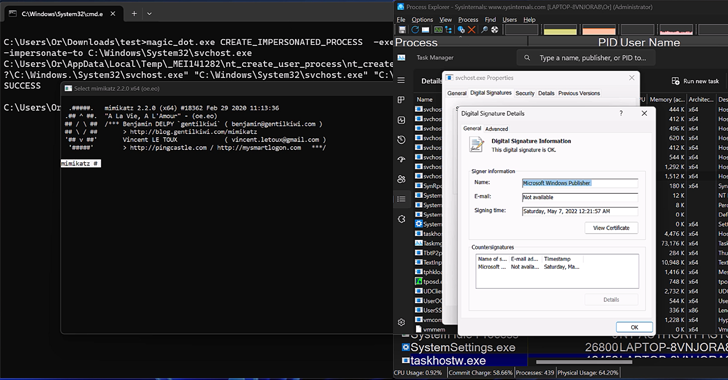
New research unveiled at the Black Hat Asia conference reveals a significant security vulnerability in the Windows DOS-to-NT path conversion process. This flaw allows threat actors to exploit the system for rootkit-like activities, such as concealing and impersonating files, directories, and processes, without needing administrative privileges. The vulnerability, identified by SafeBreach’s Or Yair, stems from the system’s handling of path conversions, where trailing dots and spaces are removed, enabling attackers to perform a range of malicious actions undetected. These actions include hiding malware, disabling Process Explorer, and impersonating legitimate Microsoft files. The discovery led to the identification of four security issues, three of which Microsoft has addressed. The vulnerabilities include an elevation of privilege for file deletion and writing, a remote code execution flaw, and a denial-of-service vulnerability affecting Process Explorer. This groundbreaking research highlights the potential for seemingly benign issues to be weaponized, posing a significant risk to Windows, the world’s most widely used desktop OS, and underscores the importance for all software vendors to address known issues promptly.
Read more at The Hacker News…